Setting up Active Directory and ADFS
IdeaScale SSO can be configured to work with Active Directory with ADFS 2.0 and 3.0 server. In supported configuration, IdeaScale will work as Service Provider (SP) and ADFS 2.0 and 3.0 server will work as Identity Provider (IdP). The supported authentication flow is SP initiated.
Steps:
-
Configure SSL in IdeaScale: ADFS 2.0 / 3.0 might require that only HTTPS protocol is used. To enable this feature, go to Security >> Access Restrictions >> SSL Security, check the checkbox “Enable SSL Security”.
-
Collect IdeaScale SP Metadata: The SP metadata is available from the URL https://[community].ideascale.com/a/saml/metadata This metadata xml file contains all required information for ADFS 2.0 / 3.0 server.
-
Configure ADFS: IdeaScale is required to be added as trusted “Relying Party” in ADFS.
Note: SSL security works out of the box for communities on .ideascaleapp.com domain. If you are using a custom domain for your community, please contact support for additional configuration.
To configure:
-
Open ADFS 2.0 / 3.0 Management Console and navigate to the Relying Parties section. Click Add Relying Party Trust and select the first option “Import data about relying party published online or on a local network”.
-
Enter the URL https://[community].ideascale.com/a/saml/metadata in the input box.
-
When asked for “Display Name” enter your community domain ([community].ideascale.com)
-
Review and proceed with subsequent steps.
-
Change Encryption Algorithm (Important): Once the relying party trust is created, edit it by right click and selecting properties menu. Goto “Advanced” tab and select “SHA-256”.
We still support SHA-1, but the default is now SHA-256
-
Configure Claim Rules: After adding the relying party trust, the wizard will ask you to configure the claim rules. You can also reconfigure later by doing right click on the relying party section and selecting the menu “Edit Claim Rules”.
-
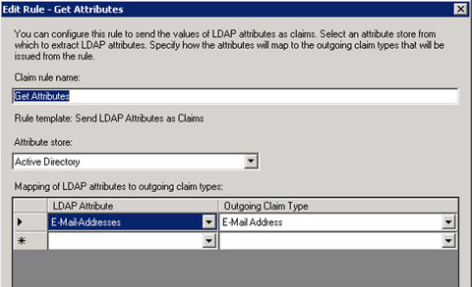
Click “Add Rules” and select “Send LDAP Attribute as Claims” and select “Active Directory” as Attribute store. Configure “E-Mail-Addresses” to map to Outgoing claim type “E-Mail Address”.
In case the email address is not passed along, users will be asked to provide it upon their first login. However they have the option to opt out for it by clicking on Skip.
-
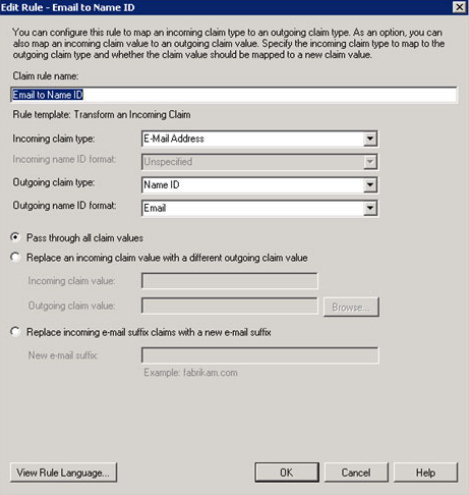
Click “Add Rule” and select “Transform an Incoming Claim”. Configure Claim rule name “Email to Name ID” or anything you feel right, Incoming claim type: “E-Mail Address”, Outgoing claim type: “NameID”, outgoing name ID format: “Email”.
-
Collect ADFS 2.0 / 3.0 IdP Metadata: The metadata XML file is generally available in https://[your-adfs-domain.com]/FederationMetadata/2007-06/Federatio... Please refer to ADFS documentation for correct location for the metadata xml.
-
Configure IdeaScale SAML: Login as “Admin/Owner” of the community and goto Security >> Single Signon Settings. Select “SAML 2.0 / 3.0” for Single-Signon Type.
-
Copy the content of ADFS 2.0 / 3.0 Metadata xml collected at Step 6. Paste the XML content to the text input box “SAML IdP Metadata”. NOTE: Incase you add Logout URL, make sure the IdP sends back a SAML LogoutResponse else user will remain on IdP page.
-
Identify the “entityID” in first few lines in ADFS metadata xml and enter that value in input “SAML IdP Entity ID”. Generally the entityID is in the format “http://[your-adfs-domain.com]/adfs/services/trust”. Please make sure you take the value carefully from XML file and provide it as it is.
-
Check the checkbox “Enabled Debugging”. This is optional but useful in case anything goes wrong. You can always remove it later.
-
Save Settings and test login by going to your community in a new browser window.
-
If anything goes wrong, look at “SSO Debugger” page in your communities “Moderation View” or https://[community].ideascale.com/a/admin/sso/debugger. Also look at the ADFS Event log for issues at ADFS server.
-
If you are using custom domain for community URL and using ADFS as IdP then SSL should be enabled for the community. If SSL is not enabled for your custom domain, you could use SSL on ideascaleapp.com domain and for that you can enable the option "Use ideascale.com secure URL for SAML".

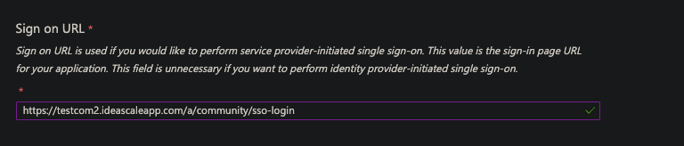
- The endpoint "/a/community/sso-login" should be used in ADFS if you want to use IDP initiated login.